MikroTik to CISCO ASA Firewall IPSEC
IMAGE step by step
Step 1
ASA firewall configuration
interface Ethernet0/0
nameif outside
security-level 0
ip address 192.168.5.121 255.255.255.0
interface Ethernet0/2
nameif dmz
security-level 50
ip address 192.168.6.1 255.255.255.0
!
access-list nonata2m extended permit ip host 192.168.6.2 host 192.168.3.254
access-list a2m extended permit ip host 192.168.6.2 host 192.168.3.254
nat (dmz) 0 access-list nonata2m
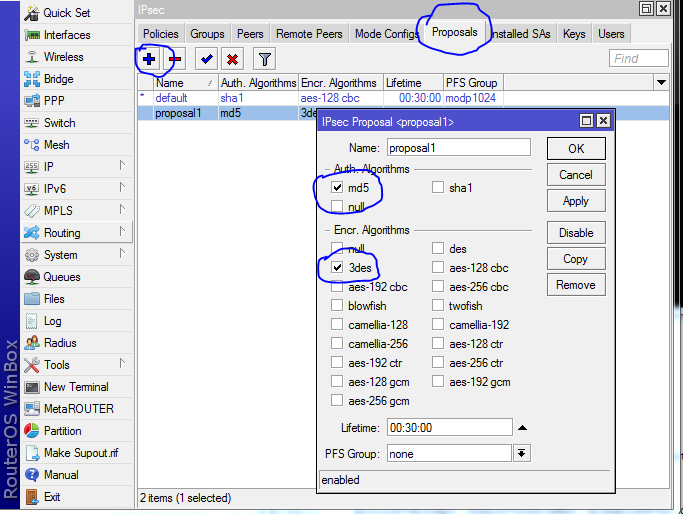
crypto ipsec transform-set asamik esp-3des esp-md5-hmac
crypto map asavpn 10 match address a2m
crypto map asavpn 10 set peer 192.168.5.1
crypto map asavpn 10 set transform-set asamik
crypto map asavpn 10 set security-association lifetime seconds 86400
crypto map asavpn interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
tunnel-group 192.168.5.1 type ipsec-l2l
tunnel-group 192.168.5.1 ipsec-attributes
pre-shared-key *
nameif outside
security-level 0
ip address 192.168.5.121 255.255.255.0
interface Ethernet0/2
nameif dmz
security-level 50
ip address 192.168.6.1 255.255.255.0
!
access-list nonata2m extended permit ip host 192.168.6.2 host 192.168.3.254
access-list a2m extended permit ip host 192.168.6.2 host 192.168.3.254
nat (dmz) 0 access-list nonata2m
crypto ipsec transform-set asamik esp-3des esp-md5-hmac
crypto map asavpn 10 match address a2m
crypto map asavpn 10 set peer 192.168.5.1
crypto map asavpn 10 set transform-set asamik
crypto map asavpn 10 set security-association lifetime seconds 86400
crypto map asavpn interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
tunnel-group 192.168.5.1 type ipsec-l2l
tunnel-group 192.168.5.1 ipsec-attributes
pre-shared-key *







No comments:
Post a Comment